Troubleshooting
This section includes solutions to common issues within the configuration of
Issabel Contact Center. Dialer Connection Failure in the Panel Manager of Issabel Contact Center
When trying to access the Dialer within the Panel Manager of
Issabel Contact Center, connection errors may appear, preventing access to this section or the creation and configuration of campaigns, groups, numbers, dispositions, among others. In most cases, the cause of such errors is related to the channel variables (channelvars) in the Asterisk configuration of the PBX. To verify this, access the PBX via SSH and execute the following command: bash
grep channelvar /etc/asterisk/manager* The following should be obtained:
bash
/etc/asterisk/manager.conf:channelvars=DIALERID,DIALERVAR If the values
To do this, access the
DIALERID and DIALERVAR are not observed, this confirms the cause of the problem. However, the best way to resolve it is not by directly modifying the Asterisk configuration file but through the PBX interface.To do this, access the
PBX administration interface with an account that has administrative permissions and navigate to PBX Configuration → Settings → Asterisk Manager Configuration. There, in the Channel Variables field, add the values: DIALERID and DIALERVAR, as shown below: 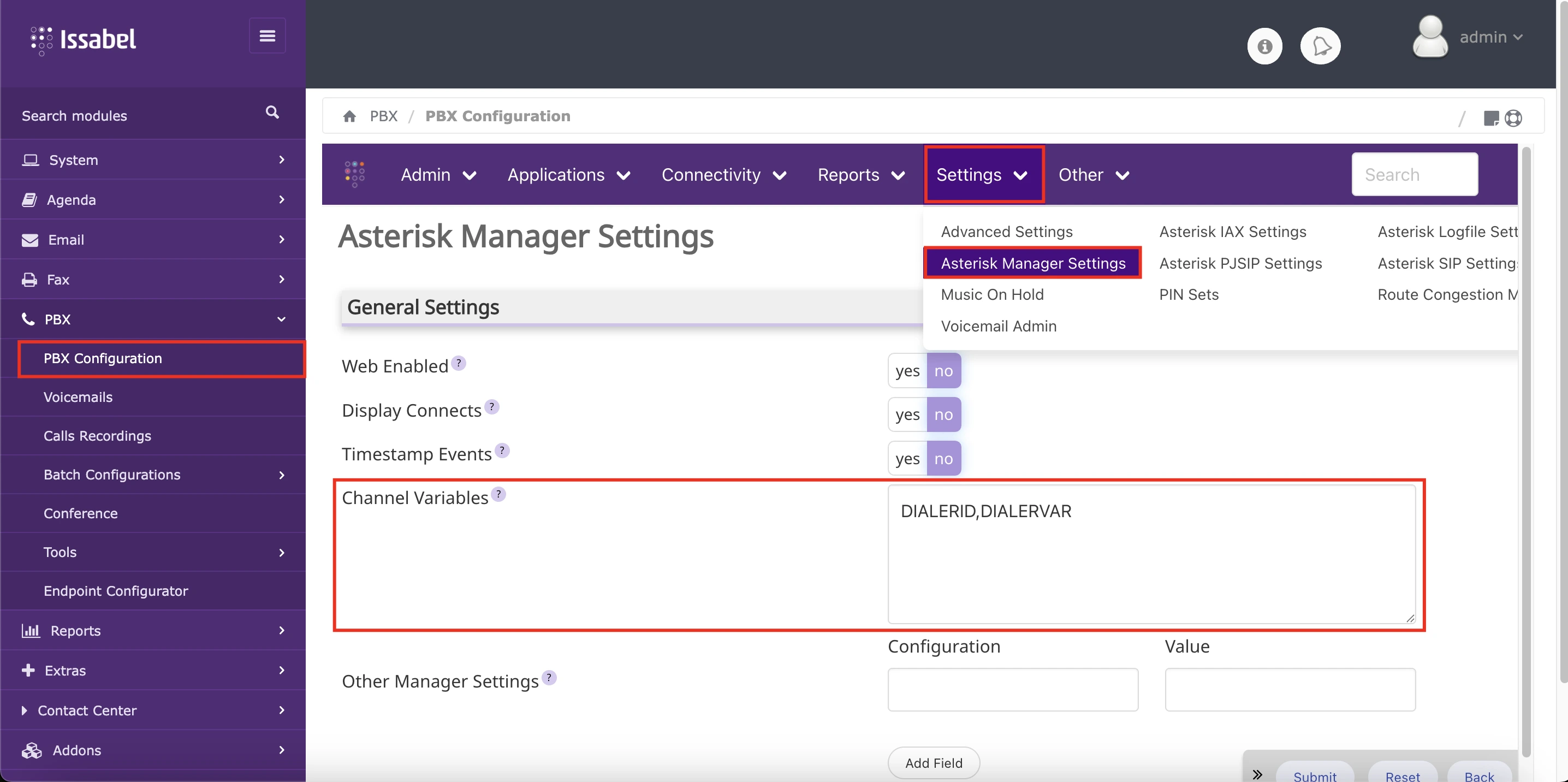
In most cases, this will resolve the connection issue with the Dialer.
System is not available right now
When trying to connect to the agent console in the
Panel Manager, the error "System is not available right now" may appear. This error can be caused by several reasons, such as the tcp/4445 port being closed in a firewall, the fop2 service not running (fop2 server stopped), or at a higher level, the SSL certificate not being configured in fop2. To verify certificate issues, execute the following command: bash
/usr/local/fop2/setSSL.sh and then:
bash
service fop2 restart It is also possible to verify the certificate paths from the fop2 configuration file with the following command:
bash
sudo cat /usr/local/fop2/fop2.cfg Within the content of this configuration file, the paths for the certificate and key corresponding to the security certificate will be found.
bash
...
; If you access fop2 via https, browsers will try to use wss (Secure
; web sockets) and for that it requires a certificate file and key file,
; the same ones you have in your web server configuration. Be sure to
; specify the correct certificates, the defaults are the ones for a
; regular Centos installation:
;
ssl_certificate_file=/etc/pki/tls/certs/localhost.crt
ssl_certificate_key_file=/etc/pki/tls/private/localhost.key
... The variable that stores the path for the SSL security certificate file is: ssl_certificate_file, and its default path is: /etc/pki/tls/certs/localhost.crt. The variable that stores the path for the SSL security certificate key is: ssl_certificate_key_file, and its default path is: /etc/pki/tls/private/localhost.key. These paths point to the self-signed certificate generated during the installation of
Issabel. It is necessary to change the content of these variables to the paths of the SSL security certificate file and key, whose location will depend on the installed certificate provider. To modify the FOP2 configuration file, execute the following command: bash
sudo vim /usr/local/fop2/fop2.cfg And modify:
bash
ssl_certificate_file=/<path_to_ssl_certificate_file>
ssl_certificate_key_file=/<path_to_ssl_certificate_key> Then, restart the FOP2 service:
bash
service fop2 restart Similarly, it is possible to verify and modify the firewall rules and restrictions as needed.
If there is any incorrect or incomplete information, or additional information needs to be generated, please write to isscc@issabel.com